Some time ago I faced with interesting problem: when tried to get properties of Azure AD group using app token with app permissions (without available user context) through Graph API:
https://graph.microsoft.com/v1.0/groups/{groupId}?$select=visibility,unseencount
the following error was shown:
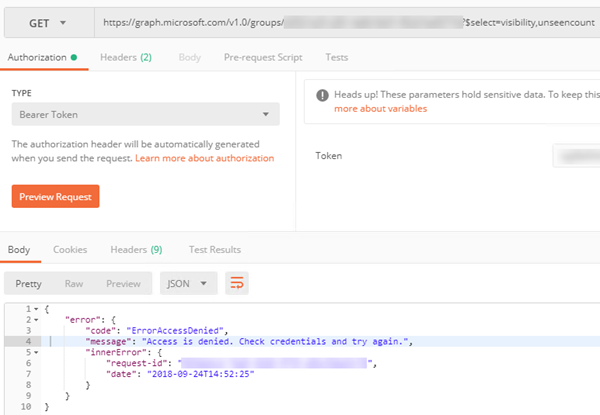
{
"error": {
"code": "ErrorAccessDenied",
"message": "Access is denied. Check credentials and try again.",
"innerError": {
"request-id": "…",
"date": "…"
}
}
}
Here is example from Postman:
Investigation showed that problem was caused by unseencount property. When I tried to remove it – another selected property (visibility) was returned successfully:
https://graph.microsoft.com/v1.0/groups/{groupId}?$select=visibility
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#groups(visibility)/$entity",
"visibility": "Public"
}
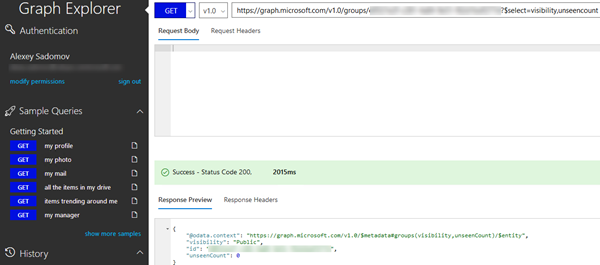
What was even more stranger is that in Graph explorer it worked:
Communication with MS support both on forums (see Can't get group's unseenCount) and via Azure support ticket helped to figure out the reason of this problem: in Postman I used app token with app permissions, while in Graph explorer I was authenticated with my own account (see above). I.e. in Graph explorer delegated permissions were used. And there is known issue in MS Graph (see Known issues with Microsoft Graph): unseencount may be retrieved only using delegated permissions:
“Examples of group features that support only delegated permissions:
- Group conversations, events, photo
- External senders, accepted or rejected senders, group subscription
- User favorites and unseen count
- Microsoft Teams channels and chats”
Hope that this information will help someone.

Check this answer on SO: https://stackoverflow.com/a/52257735/2043134
ReplyDelete